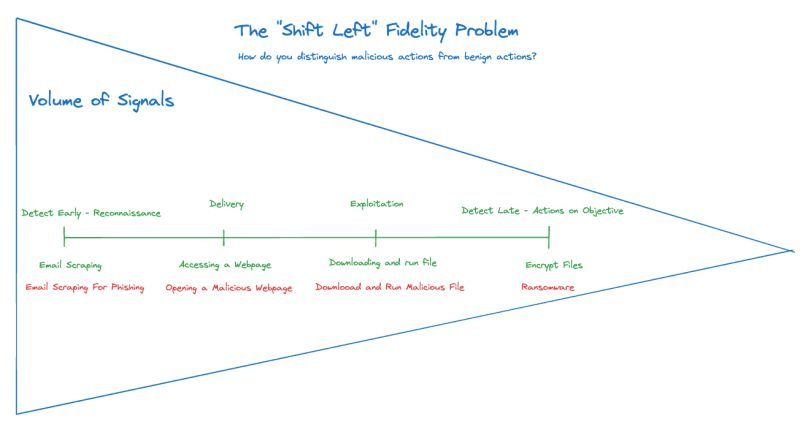
I'd like to discuss a common issue in Detection Engineering that I call "The Shift Left Fidelity Problem." This is the beginning of a more in-depth article, but for now, I aim to outline some preliminary thoughts.
The core challenge of "shifting left" in detection engineering revolves around two main hurdles: accurately discerning malicious intent and managing the overwhelming volume of alerts that require human intervention. Detection engineers are tasked with developing criteria to determine whether an activity is malicious or benign, a question that incident responders also face upon receiving an alert. In the early detection stages, such as reconnaissance, the signal-to-noise ratio is exceptionally high. At this point, deciding whether to route these signals to your SOAR or SOC becomes problematic. Often, there isn't sufficient context to distinguish between innocuous activities (like LinkedIn scraping for marketing purposes) and potentially malicious ones (scraping for phishing campaigns), leading to a high likelihood of "not evil" activity disposition.
However, as we continue down the kill chain, we're able to integrate more context. For instance, if an entity scrapes LinkedIn and subsequently sends an email containing a suspicious link, the combination of these actions reduces the volume of signals and enhances context, thus this could meet the volume threshold for incident responders to review.
So, how can we effectively enrich a high volume of signals with enough context to not only deduce malicious intent but also assess the potential for reconnaissance activities to escalate further? It's clear we need to avoid routing common activities like scraping, yet remain keen to the possibility of the activity foreshadowing advancement along the kill chain.
I plan to introduce solutions or conceptual strategies to mitigate this challenge in longer form in the future, but for now what are your thoughts on this problem?